Cyber threats and cyber influencing
Updated December 2025
- The latest hybrid influencing tool and form of threat
- Targeting information networks
- There are three types of malicious cyber activity: cyber intelligence (espionage), cyber-attacks, and data manipulation
- the purpose of cyber intelligence: collect information,
- cyber-attacks – especially concerning the network infrastructures of society’s electricity, communications, water, financial and critical systems,
- the purpose of cyber manipulation: change the information stored on networks.
- Recent trends
- ransom-demanding malware campaigns,
- cyber threats stemming from component and device vulnerabilities,
- covert military operations in cyberspace,
- information networking as a new form of conflict between states,
- the use of new technologies such as ORB networks,
- increased operational effectiveness of Chinese groups,
-
- Israel’s “pager strike” against Hezbollah,
- critical infrastructure in many countries compromised, allowing vulnerabilities to be implanted in networks – vulnerabilities that could later be activated.
- Cyber activities in the Russia-Ukraine war since 2022
Read more
This latest hybrid influencing tool and form of threat is still the most difficult to grasp, even though it has been used for twenty years. There are three ways to target cyber networks with malicious cyber activity: intelligence (espionage), attacks, and data manipulation (processing).
Cyber intelligence is like traditional intelligence and espionage activities, the purpose of which is to gather information. The information stolen through cyber intelligence may be kept secret for one’s own needs, or leaked for influencing purposes (e.g., Wiki Leaks) as part of hybrid influencing.
Two known hacker groups (APT 28 / Fancy Bear and APT 29 / Cozy Bear) with ties to Russian intelligence services are known to have carried out hostile espionage operations on the computer networks of other states. In 2015, APT 29 infiltrated the U.S. White House data network, as well as the networks of several organisations in Western Europe, Central and Eastern Asia, and Central and South America. APT 28 was also found to have broken into the networks of military and defence companies in America, Europe and Asia. It was also behind the intrusion into the networks of the German Reichstag and French TV5 Monde in 2015.
Covert data collection is not new, but the cyber dimension brings new tools and reduces costs. Cyber operations are low-cost, low-risk, and can yield good results – thus making them attractive to poorer countries as well.
A cyber-attack is a continuum of cyber intelligence and refers to an attack that targets, in particular, the cyber infrastructures of society’s electricity, communications, water, financial and critical systems. So far, there have been relatively few of them – but this activity has increased considerably in recent years.
The discovery of Stuxnet in Iranian computer systems in 2010 marked the introduction of a new type of cyber warfare method. This “world’s first digital weapon” differed from previous cyber malware in that, in addition to stealing data, it destroyed the physical devices controlled by computers. There were two different versions of the attack: the first damaged centrifuges at Iran’s nuclear enrichment plants, and the second manipulated the computer systems of those companies that were supplying Iran’s nuclear programme with industrial control and processing systems.
One of the most troubling cases has been the successful attack on the computer network of the Canadian company, Telvent (APT 1 / Comment Crew / Comment Panda), by a cyber task force linked to the Chinese army unit 61398. The Telvent company designs remote access software for valves, switches and safety systems for oil and gas pipeline companies and power grid operators. Telvent maintains detailed plans for more than half of all oil and gas pipelines in North and South America and has access to their systems.
Cyber-attacks on critical infrastructure, especially power grids, have occurred in connection with almost all recent political and military crises, including Estonia 2007, the Balkans, Georgia 2008, Ukraine since 2014, Syria and the rest of the Middle East.
In cyber manipulation, hacker groups can manipulate or alter data stored on a network, once they gain access to the system. Manipulation can be a serious challenge in the future. So far, most cyber intrusions have been data theft. The threat is that the intruder will start manipulating and modifying the data so that the network owner can no longer believe in, and trust, their own system. One of the most serious incidents of electronic manipulation occurred in 2013, when Syrian hackers gained access to the Associated Press Twitter account and tweeted false news about the White House explosion. This also had a direct impact on US stock prices. One of the first attempts to manipulate data to achieve political goals occurred during the 2016 US presidential election. Russian hackers who had gained access to the Illinois state’s voter database attempted to change the registry information – but, fortunately, without success.
Recent trends
During 2017, many cases of ransomware (WannaCry, NotPetya and BadRabbit) occurred in almost epidemic style. In 2018, it became clear how limited our capabilities are, in dealing with cyber threats related to side-channel attacks and vulnerabilities in microprocessors and various components and devices (tamped). Since 2019, covert military operations related to interstate conflicts have increasingly begun to take place in cyberspace, with the result that cyber researchers worldwide – ranging from financially motivated cyber criminals to state-sponsored cyber researchers – have begun to focus ever-increasing attention on it.
In recent years, the Internet of Things (IoT) has introduced a new dimension to the cyber world that can be utilised in cyber operations. Due to the low level of security in these devices, it is possible to access computer networks and spread malware through them.
The latest attack method has been the use of the so-called Operational Relay Box (ORB) networks. An ORB network is a controlled infrastructure made up of different devices that are used to carry out cyberattacks while concealing their activities. These botnet-like networks rely on rented virtual private servers (VPS) and compromised devices such as IoT devices, smart devices, and routers. A key difference from traditional botnets is the decentralized and self-sustaining nature of ORBs, which makes them more difficult to detect and block.
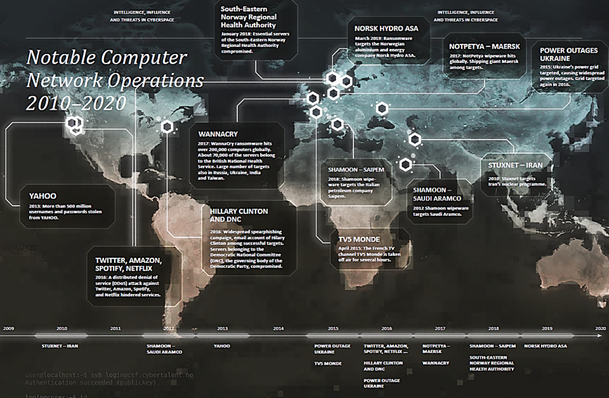
Image source: Focus 2020. The Norwegian Intelligence Service’s assessment of current security challenges.
The focus of the cyber activities of states and the groups supported by them is intelligence. There are nearly 200 such groups around the world, backed by organisations from 20 countries, including China, India, Iran, Israel, Kazakhstan, Lebanon, Nigeria, Pakistan, Palestine, North Korea, Syria, Russia, Vietnam, Turkey, the United Arab Emirates and the United States. Several Western countries, such as Britain, France, Germany and the United States, operate in cyberspace through actors that are part of their intelligence and defence organisations.
Cyber operations, combined with other hybrid influencing methods, have provided states with opportunities to act in ways that can be conducted at least to some extent in secret, and so that their involvement in cases that come to light can be denied. Offensive cyber operations have been used especially in connection with the war in Ukraine and the related occupation of Crimea, as well as in the Middle East in connection with the Syrian civil war and the situation in Iran.
 Image source: Estonian Foreign Intelligence Service, 2018Concerning state-sponsored cyber operations, Russian and Chinese actors are the most active and have caused the greatest damage. Since 2014, their main targets of the Russian actors have been the Ukrainian government and its law enforcement agencies and armed forces. Since 2017, Russian activities have also been targeted against critical infrastructure and energy sectors (nuclear power plants, for example) in Europe and the United States. At least seven Russian groups, operating under varying names, have been identified.
Image source: Estonian Foreign Intelligence Service, 2018Concerning state-sponsored cyber operations, Russian and Chinese actors are the most active and have caused the greatest damage. Since 2014, their main targets of the Russian actors have been the Ukrainian government and its law enforcement agencies and armed forces. Since 2017, Russian activities have also been targeted against critical infrastructure and energy sectors (nuclear power plants, for example) in Europe and the United States. At least seven Russian groups, operating under varying names, have been identified.
Chinese groups have been found to focus mainly on the requirements set out in the government’s “Made in China 2025” plan for the technology, energy and healthcare sectors. In recent years, a significant increase in the activity of Chinese groups has been observed, which is, at least partly, related to the deterioration of US-China relations. The most active groups are APT40 and Mustang Panda, which generated almost half of all observed activity. In addition, the activity of the Chinese APT41 group increased significantly in the first quarter of 2025.
Chinese actors have significantly developed and refined their tactics to remain effective while minimizing the risks of exposure. The operating methods have become more sophisticated. Zero-day vulnerabilities and known vulnerabilities in commonly used network peripherals were heavily relied on instead of traditional methods such as phishing and social engineering. Additionally, the use of ORB networks in attacks increased significantly.
In recent years, Iranian groups have enhanced their activities with new tactics, techniques and procedures. These include, for example, strategic web compromise campaigns and mobile malware which have been used against regional rivals, in order to restrict the activities of opposition groups in the country and to support their own “soft war” campaigns. Iran’s cyber operations focused mainly on espionage, information warfare, and various disruptive activities. The activities of Iranian-linked groups increased in February 2025 as the United States reimposed sanctions and increased isolation and military pressure on Tehran.
North Korean groups have also increased their activity recently. Their targets have included the financial sector and intelligence operations in South Korea.
An example of an offensive cyber operation is also the so-called triggered thousands of pager strike carried out by Israel against Hezbollah in September 2024. Mossad pre-manipulated pagers and hundreds of walkie-talkies to explode in the hands of Hezbollah members across Lebanon and Syria. Several people died, and about 3,000 people were wounded in the operation.
Cyber activities in the Russia-Ukraine war since 2022
The war between Russia and Ukraine has involved cyber warfare to an unprecedented extent. Russian cyber groups have been particularly active in intelligence gathering and through disinformation aimed at influencing the general mood in Ukraine and destroying state and commercial networks. Large-scale Russian-patriotic hacktivism has also been observed behind these activities in line with Russia’s ambitions, and Western actors have often been targeted.
Russia has long integrated cyber activities with its military operations – in particular, through distributed denial-of-service (DDoS) attacks. Activities since 2022 show that Russia is using a wide range of tools to achieve its goals.

Russia’s cyber activities against Ukraine in 2022. Image source: Crowdstrike Global Threat Report (2023)
The accompanying chart shows how the levels of Russian cyber activity changed during 2022. The activities are divided into intelligence gathering, disinformation operations and network destruction activities.
Ukrainian cyber actors have also retaliated against the Russian state and its allies throughout 2022. Russia’s military intelligence service, the GRU, appears to be responsible for many operations against Ukraine, but the FSB (the federal security service) has also supported the war by collecting intelligence. Cyber Action Teams were particularly active against Ukraine in 2022. Other, unidentified operations also targeted Ukrainian organisations and individuals for the probable purpose of gathering intelligence. They usually used phishing methods to gain access to email accounts.
In January 2022, prior to Russia’s invasion of Ukraine, ongoing reconnaissance activities aimed at Ukrainian targets were complemented by several devastating EMBER BEAR operations which defaced websites and spread malware. This was probably intended to weaken the Ukrainian Government’s ability to act. In addition, it involved attempts to psychologically influence Ukrainian citizens by claiming that the Ukrainian authorities would not be able to protect them in the case of a military incursion.
In February 2022, several DDoS attacks targeted Ukrainian government portals and financial institutions. The aim was to put pressure on Ukrainian citizens by interrupting their use of banking services. Western sources stated that at least some of the attacks were carried out by the GRU.
After the invasion began, Russia conducted several secret, destructive operations against Ukrainian computer networks. The aim was to deny Ukrainians access to energy supplies or state databases, for example, but covertly, without attracting public attention. Instead, the EMBER BEAR operations were carried out openly against Ukrainian government websites, and reports were made of data destruction and the leaking of public information, suggesting that this was a hacktivist activity.
On 23 February 2022, Russian cyber actors launched several attacks against Ukraine’s network infrastructure. The attacks used unprecedented, unique and highly destructive malware families and corrupted websites. In addition, within 48 hours, new data-destroying malware families (DriveSlayer, PartyTicket, IsaacWiper and AcidRain) were deployed in tandem with the military invasion launched by Russia on 24/02/2022.
AcidRain was deployed less than one hour after President Putin announced the start of a “special military operation”. This is noteworthy because it seemed specifically designed to interfere with the network segments of Viasat satellite communications – those segments that provide network access to Ukraine.
The actual impact of cyber operations on the Ukrainian government and armed forces is unclear, but it was felt beyond Ukraine’s borders. This disruption affected service providers across Europe, leading to outages for thousands of customers and disruptions in wind turbine network communications in some locations in Germany.
After the first week of war, Russia’s cyberattack activity intensified, although its capabilities and range of tools began to decline. The exception was VOODOO BEAR’s activities, which included the deployment of CaddyWiper, which began on 14 March 2022 and continued throughout the year, as well as attacks on Ukraine’s energy sector with the new CrashOverride program and several functions designed to wipe Linux and Solaris systems.
In the second half of 2022, Russian cyber activity shifted to focus more on intelligence gathering operations. This points to the needs of the military and Kremlin for greater situational awareness as the invasion of Ukraine stalled.
The identified operations included extensive attempts by Russian cyber task forces to phish for information on Ukrainian targets. Phishing activities have extensively targeted state actors such as laboratories, military equipment suppliers, logistics companies and NGOs. This reflects Russia’s efforts to gather intelligence on Western military support for Ukraine. Targeting NGOs may indicate a desire to retaliate against any organisations that may be involved in Russian war crimes investigations. Despite the emphasis on intelligence gathering, Russia’s devastating malware families, Prestige and RansomBoggs, disguised as ransomware, were deployed in October and November 2022.
The use of fake ransomware suggests that Russia intends to direct its cyber activity more towards targets where destructive operations are considered politically risky. The overall impact of Russia’s cyber activities in the context of the invasion of Ukraine is unclear. Russian cyber actors have participated in the military operation, and there have been wartime restrictions on operations. Devastating attacks often require extensive planning but are less effective than conventional warfare.
The war in Ukraine has not lived up to expectations of how cyber operations can support modern warfare. Attacks on key industries such as energy, telecommunications, transportation and media have not been as widespread as predicted. This suggests in part that Russia expected a swift and decisive victory over Ukraine and that functioning systems were needed in order to keep Ukraine running under the new regime.
At the end of 2024 and the start of 2025, the intensity of the war escalated. Both sides stepped up their hybrid warfare, especially cyberattacks, disinformation campaigns and economic warfare. Russia developed cyber capabilities against Ukraine’s critical infrastructure, targeting energy networks, financial systems, and government communications. Ukraine strengthened its cyber defence and launched offensive cyber operations against Russian targets.
The activities of the Russian Sandworm group, also known as APT44, increased significantly at the end of 2024, particularly during August. Sandworm is one of the most capable cyber groups sup-porting Russian military operations. During this period, Russia also carried out its largest missile and drone strikes against Ukraine since the start of the conflict. These cyber operations were timed to coincide with missile and drone strikes, amplifying the impact of the physical attacks. The con-vergence of cyber and kinetic operations reflects a growing trend in hybrid warfare, in which state actors use physical and digital means simultaneously to achieve larger strategic goals.
Concerns in the early stages of the war about significant collateral damage to international networks were also not fully realized. The identified attacks mostly targeted Ukrainian networks. Nevertheless, sectors that have not been targeted until now may still be targeted as the war continues.
Ukraine has employed a well-functioning cyber defence. Ukraine, in cooperation with private actors and with the support of its allies, has succeeded in preventing and undermining many of Russia’s devastating cyber operations.
Sources and links
National and multinational government organisations:
- The European Centre of Excellence for Countering Hybrid Threats (Hybrid CoE):
https://www.hybridcoe.fi/ - European Union Institute for Strategic Studies (EUISS):
https://www.iss.europa.eu/) - The State Security Department of Lithuania:
https://www.vsd.lt/en/threats/threats-national-security-lithuania/
- US Cybersecurity & Infrastructure Security Agency, CISA (US CERT, Department of Homeland Security & Federal Bureau of Investigation):
https://us-cert.cisa.gov/
Private companies and organisations monitoring and investigating cyber activity:
- CrowdStrike:
https://www.crowdstrike.com/en-us/ - Trellix:
trellix.com
- Palo Alto Networks Unit 42:
https://unit42.paloaltonetworks.com/
